Difference between revisions of "Social Network Analysis"
(→War on Terror) |
John Cross (talk | contribs) |
||
| (20 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| − | '''Social Network Analysis''' is a key component of [[Power Structure Research]]. | + | '''Social Network Analysis''' is a key component of [[Power Structure Research]]. it 'is the mapping and measuring of relationships and flows between people, groups, organizations, computers, web sites, and other information/knowledge processing entities.'<ref>[http://www.orgnet.com/sna.html Social Network Analysis, A Brief Introduction], orgnet.com, accessed 19 Mar 2010</ref> |
| − | [[Image:Freamon, SNA clocks.jpg|right|thumb|400px|Freamon works out the hidden connection in the network]] | + | [[Image:Freamon, SNA clocks.jpg|right|thumb|400px|Freamon works out the hidden connection in the network in ''The Wire'']] |
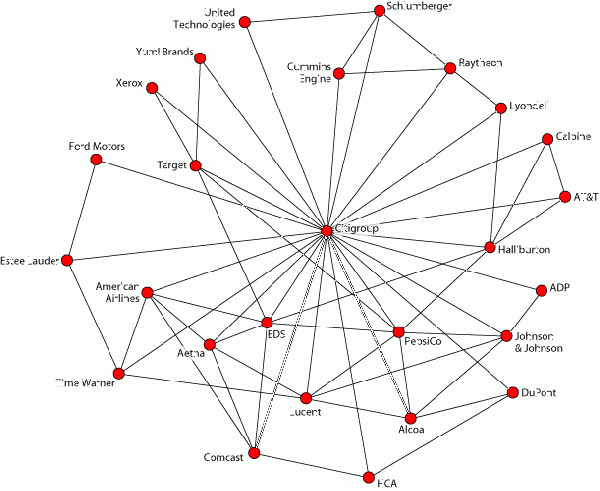
| + | [[Image:Citigroup corp NetDraw.gif|thumb|right|600px|The Citigroup network of interlocks (Image from Domhoff <ref>G William Domhoff 2005 http://sociology.ucsc.edu/whorulesamerica/powe/corporate_community.html Interlocking Directorates in the Corporate Community] ''Who Rules America?'' August</ref>)]]According to the orgnet.com website: | ||
| + | :The nodes in the network are the people and groups while the links show relationships or flows between the nodes. SNA provides both a visual and a mathematical analysis of human relationships. Management consultants use this methodology with their business clients and call it [[Organizational Network Analysis]] [ONA]. | ||
| − | == | + | :To understand networks and their participants, we evaluate the location of actors in the network. Measuring the network location is finding the centrality of a node. These measures give us insight into the various roles and groupings in a network -- who are the connectors, mavens, leaders, bridges, isolates, where are the clusters and who is in them, who is in the core of the network, and who is on the periphery?<ref>[http://www.orgnet.com/sna.html Social Network Analysis, A Brief Introduction], orgnet.com, accessed 19 Mar 2010</ref> |
| + | |||
| + | ==Uses== | ||
| + | ===Corporate Interlocks=== | ||
| + | |||
| + | 'Interlocking directorates -- defined as the linkages among corporations created by individuals who sit on two or more corporate boards -- have been a source of research attention since the Progressive Era at the turn of the 20th century,' writes William Domhoff. Then 'they were used by famous muckraking journalists, and future Supreme Court Justice Louis Brandeis, to claim that a few large commercial and investment banks controlled most major corporations.'<ref>G William Domhoff 2005 [http://sociology.ucsc.edu/whorulesamerica/powe/corporate_community.html Interlocking Directorates in the Corporate Community] ''Who Rules America?'' August</ref> | ||
| − | + | Domhoff goes on to note that: | |
| − | |||
| − | : | + | :Today corporate interlocks are analyzed with bigger databases and sophisticated network programs, thanks to desktop computers. The databases are large matrices that contain information on the linkages between persons and groups. Either a corporate/organizational network, based on common directors, or an interpersonal/social network, based on shared board memberships, can be derived from these matrices. That is, the matrices contain a "duality of persons and groups".<ref>Breiger R. L. (1974). The duality of persons and groups. ''Social Forces'', 53, 181-190.</ref> This is worth mentioning because this essay will discuss both "corporate networks," that is, the linkages among corporations created by interlocking directorates, and "social networks," that is, the linkages among people by virtue of the fact that they sit on the same corporate board.<ref>G William Domhoff 2005 [http://sociology.ucsc.edu/whorulesamerica/powe/corporate_community.html Interlocking Directorates in the Corporate Community] ''Who Rules America?'' August</ref> |
| − | |||
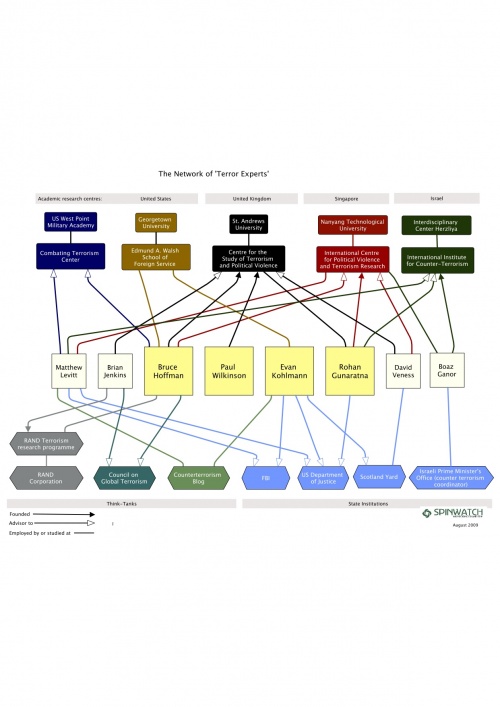
===War on Terror=== | ===War on Terror=== | ||
| + | [[Image:Step 1.gif|thumb|right|600px|Mapping 'Terror' networks<ref>[http://www.orgnet.com/tnet.html Connecting the Dots Tracking Two Identified Terrorists] by Valdis Krebs, Orgnet.com, Original, 2002, updated in 2005, 2006, 2007</ref>]] | ||
| + | Krebs discusses how to use these techniques in plotting 'terror' networks: | ||
| − | |||
:Social Network Analysis [SNA] is a mathematical method for 'connecting the dots'. SNA allows us to map and measure complex, and sometimes covert, human groups and organizations. Early in 2000, the CIA was informed of two terrorist suspects linked to al-Qaeda. Nawaf Alhazmi and Khalid Almihdhar were photographed attending a meeting of known terrorists in Malaysia. After the meeting they returned to Los Angeles, where they had already set up residence in late 1999. | :Social Network Analysis [SNA] is a mathematical method for 'connecting the dots'. SNA allows us to map and measure complex, and sometimes covert, human groups and organizations. Early in 2000, the CIA was informed of two terrorist suspects linked to al-Qaeda. Nawaf Alhazmi and Khalid Almihdhar were photographed attending a meeting of known terrorists in Malaysia. After the meeting they returned to Los Angeles, where they had already set up residence in late 1999. | ||
| Line 23: | Line 29: | ||
:The structure of their extended network begins to emerge as data is discovered via surveillance. A suspect being monitored may have many contacts -- both accidental and intentional. We must always be wary of 'guilt by association'. Accidental contacts, like the mail delivery person, the grocery store clerk, and neighbor may not be viewed with investigative interest. Intentional contacts are like the late afternoon visitor, whose car license plate is traced back to a rental company at the airport, where we discover he arrived from Toronto (got to notify the Canadians) and his name matches a cell phone number (with a Buffalo, NY area code) that our suspect calls regularly. This intentional contact is added to our map and we start tracking his interactions -- where do they lead? As data comes in, a picture of the terrorist organization slowly comes into focus.<ref>[http://www.orgnet.com/tnet.html Connecting the Dots Tracking Two Identified Terrorists] by Valdis Krebs, Orgnet.com, Original, 2002, updated in 2005, 2006, 2007</ref> | :The structure of their extended network begins to emerge as data is discovered via surveillance. A suspect being monitored may have many contacts -- both accidental and intentional. We must always be wary of 'guilt by association'. Accidental contacts, like the mail delivery person, the grocery store clerk, and neighbor may not be viewed with investigative interest. Intentional contacts are like the late afternoon visitor, whose car license plate is traced back to a rental company at the airport, where we discover he arrived from Toronto (got to notify the Canadians) and his name matches a cell phone number (with a Buffalo, NY area code) that our suspect calls regularly. This intentional contact is added to our map and we start tracking his interactions -- where do they lead? As data comes in, a picture of the terrorist organization slowly comes into focus.<ref>[http://www.orgnet.com/tnet.html Connecting the Dots Tracking Two Identified Terrorists] by Valdis Krebs, Orgnet.com, Original, 2002, updated in 2005, 2006, 2007</ref> | ||
| + | Of course the same techniques can also be used to plot 'Counter-terror' network of terror experts and their connections. | ||
| + | |||
| + | [[Image:Network of terror experts new.jpg|thumb|right|500px|Image Created by Spinwatch August 2009]] | ||
===Marketing and data mining=== | ===Marketing and data mining=== | ||
| + | According to an article for Realwire: | ||
:Sales, marketing and customer retention campaigns are set to become smarter, more effective and more profitable thanks to a new social network analysis module from data mining automation vendor KXEN. By exploiting the connections between customers of telcos, banks, retailers and others, KXEN’s new KSN module has shown more than 15% lift improvement in campaign results. | :Sales, marketing and customer retention campaigns are set to become smarter, more effective and more profitable thanks to a new social network analysis module from data mining automation vendor KXEN. By exploiting the connections between customers of telcos, banks, retailers and others, KXEN’s new KSN module has shown more than 15% lift improvement in campaign results. | ||
| Line 29: | Line 39: | ||
:Using KSN, companies can increase the accuracy and precision of their campaigns by leveraging the many more customer attributes that the module reveals, allowing them to better predict when customers may be about to churn to another provider, close an account, or buy a new product. A feature unique to KXEN allows the analysis of multiple networks and their evolution over time, exposing specific patterns of behaviors like rotational churn, fraud and identity theft.<ref>[http://www.your-story.org/new-social-network-analysis-module-strengthens-kxen-automated-data-mining-6042/ New Social Network Analysis Module Strengthens KXEN Automated Data Mining] 24.03.2009 | Author: RealWire </ref> | :Using KSN, companies can increase the accuracy and precision of their campaigns by leveraging the many more customer attributes that the module reveals, allowing them to better predict when customers may be about to churn to another provider, close an account, or buy a new product. A feature unique to KXEN allows the analysis of multiple networks and their evolution over time, exposing specific patterns of behaviors like rotational churn, fraud and identity theft.<ref>[http://www.your-story.org/new-social-network-analysis-module-strengthens-kxen-automated-data-mining-6042/ New Social Network Analysis Module Strengthens KXEN Automated Data Mining] 24.03.2009 | Author: RealWire </ref> | ||
| − | |||
===Fetishising Social Network Analysis=== | ===Fetishising Social Network Analysis=== | ||
| Line 39: | Line 48: | ||
===Resources=== | ===Resources=== | ||
| + | ====Email list==== | ||
| + | |||
*Jiscmail list [https://www.jiscmail.ac.uk/cgi-bin/webadmin?A0=SNA SNA] 'The list will facilitate discussion of social network analysis amongst interested UK academics, and will facilitate organisation of off-line meetings.' | *Jiscmail list [https://www.jiscmail.ac.uk/cgi-bin/webadmin?A0=SNA SNA] 'The list will facilitate discussion of social network analysis amongst interested UK academics, and will facilitate organisation of off-line meetings.' | ||
| + | ====Software sources and information==== | ||
| + | *[http://www.social-network-blog.com/ Social Netwotk Blog] | Wikipedia [http://en.wikipedia.org/wiki/Social_network_analysis_software Social network analysis software] | | ||
| + | |||
====Visualisation==== | ====Visualisation==== | ||
*http://sourceforge.net/projects/socnetv | *http://sourceforge.net/projects/socnetv | ||
| + | *Mark Lombardi [http://www.pierogi2000.com/flatfile/lombardi.html Global Networks] | ||
====Data sources==== | ====Data sources==== | ||
* Letters written on behalf and in support of Scooter Libby to the judge that sat on his case: http://online.wsj.com/public/resources/documents/libbyletters20070605.pdf | * Letters written on behalf and in support of Scooter Libby to the judge that sat on his case: http://online.wsj.com/public/resources/documents/libbyletters20070605.pdf | ||
==Further Reading== | ==Further Reading== | ||
| + | *G william Domhoff [http://sociology.ucsc.edu/whorulesamerica/methods/how_to_do_power_structure_research.html How to do Power Structure Research], ''Who Rules America'', May 2009. | ||
*Robert A. Hanneman and Mark Riddle (2005) [http://faculty.ucr.edu/~hanneman/nettext/ Introduction to social network methods] Riverside, CA: University of California, Riverside ( published in digital form at http://faculty.ucr.edu/~hanneman/ ) | *Robert A. Hanneman and Mark Riddle (2005) [http://faculty.ucr.edu/~hanneman/nettext/ Introduction to social network methods] Riverside, CA: University of California, Riverside ( published in digital form at http://faculty.ucr.edu/~hanneman/ ) | ||
*http://www.humanities.wisc.edu/programs/Faculty-Development-Seminars/representing-culture1/reading-list.html | *http://www.humanities.wisc.edu/programs/Faculty-Development-Seminars/representing-culture1/reading-list.html | ||
*[http://www.humanities.wisc.edu/assets/files/fdsh/Representing%20Culture/Scott.pdf Scott, Social Network Analysis (excerpts)] | *[http://www.humanities.wisc.edu/assets/files/fdsh/Representing%20Culture/Scott.pdf Scott, Social Network Analysis (excerpts)] | ||
| + | *[http://www.humanities.wisc.edu/assets/files/fdsh/Representing%20Culture/Scott_Supplemental.pdf Scott Supplemental readings] | ||
*[http://faculty.ucr.edu/~hanneman/nettext/Bibliography.html Bibliography] This page is part of an on-line text by Robert A. Hanneman (Department of Sociology, University of California, Riverside) and Mark Riddle (Department of Sociology, University of Northern Colorado). | *[http://faculty.ucr.edu/~hanneman/nettext/Bibliography.html Bibliography] This page is part of an on-line text by Robert A. Hanneman (Department of Sociology, University of California, Riverside) and Mark Riddle (Department of Sociology, University of Northern Colorado). | ||
| + | *Stephen P. Borgatti, Ajay Mehra, Daniel J. Brass, Giuseppe Labianca, et al 2009 [http://www.stats.ox.ac.uk/~snijders/ Network Analysis in the Social Sciences] Science 323, 892-895 (2009). | ||
| + | *Tom Snijders [http://stat.gamma.rug.nl/socnet.htm Social Network Analysis] Website with details of information and downloads | ||
| + | *Steve Borgatti's [http://www.analytictech.com/networks/ Instructional Social Network Analysis Website.] | ||
| + | *Stanley Wasserman and Katherine Faust , Social Network Analysis: Methods and Applications. Cambridge University Press, 1994. | ||
| + | *Peter Carrington, John Scott, Stanley Wasserman (eds.), Models and Methods in Social Network Analysis. Cambridge University Press, 2005. | ||
| + | *Alain Degenne and Michel Forse, Introducing Social Networks. Sage, 1999. | ||
| + | *John Scott, Social Network Analysis: A Handbook. 2nd edition. Sage, 2000. | ||
| + | *Wouter de Nooy, Andrej Mrvar, and Vladimir Batagelj, Exploratory Social Network Analysis with Pajek. Cambridge University Press, 2005 | ||
| + | *The Back of the Napkin Blog [http://digitalroam.typepad.com/digital_roam/2006/04/antisocial_netw.html Anti-social network analysis] April 08, 2006 | ||
| + | ==See Also== | ||
| + | *[[Power Structure Research]] | [[Investigative Research]] | [[Citation Analysis]] | [[Online Ethnography]] | | ||
| − | |||
| − | |||
==Notes== | ==Notes== | ||
<references/> | <references/> | ||
| Line 59: | Line 85: | ||
[[Category:Research]] | [[Category:Research]] | ||
| + | [[Category:Investigative Research]] [[Category:Research Methods]] | ||
Latest revision as of 22:37, 7 March 2013
Social Network Analysis is a key component of Power Structure Research. it 'is the mapping and measuring of relationships and flows between people, groups, organizations, computers, web sites, and other information/knowledge processing entities.'[1]
According to the orgnet.com website:
- The nodes in the network are the people and groups while the links show relationships or flows between the nodes. SNA provides both a visual and a mathematical analysis of human relationships. Management consultants use this methodology with their business clients and call it Organizational Network Analysis [ONA].
- To understand networks and their participants, we evaluate the location of actors in the network. Measuring the network location is finding the centrality of a node. These measures give us insight into the various roles and groupings in a network -- who are the connectors, mavens, leaders, bridges, isolates, where are the clusters and who is in them, who is in the core of the network, and who is on the periphery?[3]
Contents
Uses
Corporate Interlocks
'Interlocking directorates -- defined as the linkages among corporations created by individuals who sit on two or more corporate boards -- have been a source of research attention since the Progressive Era at the turn of the 20th century,' writes William Domhoff. Then 'they were used by famous muckraking journalists, and future Supreme Court Justice Louis Brandeis, to claim that a few large commercial and investment banks controlled most major corporations.'[4]
Domhoff goes on to note that:
- Today corporate interlocks are analyzed with bigger databases and sophisticated network programs, thanks to desktop computers. The databases are large matrices that contain information on the linkages between persons and groups. Either a corporate/organizational network, based on common directors, or an interpersonal/social network, based on shared board memberships, can be derived from these matrices. That is, the matrices contain a "duality of persons and groups".[5] This is worth mentioning because this essay will discuss both "corporate networks," that is, the linkages among corporations created by interlocking directorates, and "social networks," that is, the linkages among people by virtue of the fact that they sit on the same corporate board.[6]
War on Terror
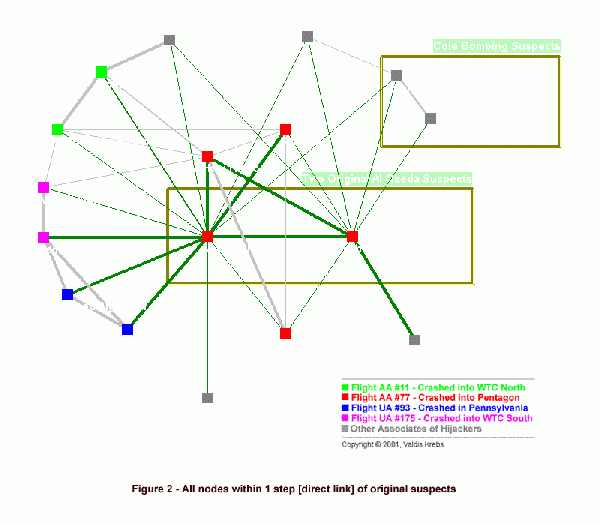
Krebs discusses how to use these techniques in plotting 'terror' networks:
- Social Network Analysis [SNA] is a mathematical method for 'connecting the dots'. SNA allows us to map and measure complex, and sometimes covert, human groups and organizations. Early in 2000, the CIA was informed of two terrorist suspects linked to al-Qaeda. Nawaf Alhazmi and Khalid Almihdhar were photographed attending a meeting of known terrorists in Malaysia. After the meeting they returned to Los Angeles, where they had already set up residence in late 1999.
- What do you do with these suspects? Arrest or deport them immediately? No, we need to use them to discover more of the al-Qaeda network. Once suspects have been discovered, we can use their daily activities to uncloak their network. Just like they used our technology against us, we can use their planning process against them. Watch them, and listen to their conversations to see...
- 1. who they call / email
- 2. who visits with them locally and in other cities
- 3. where their money comes from
- The structure of their extended network begins to emerge as data is discovered via surveillance. A suspect being monitored may have many contacts -- both accidental and intentional. We must always be wary of 'guilt by association'. Accidental contacts, like the mail delivery person, the grocery store clerk, and neighbor may not be viewed with investigative interest. Intentional contacts are like the late afternoon visitor, whose car license plate is traced back to a rental company at the airport, where we discover he arrived from Toronto (got to notify the Canadians) and his name matches a cell phone number (with a Buffalo, NY area code) that our suspect calls regularly. This intentional contact is added to our map and we start tracking his interactions -- where do they lead? As data comes in, a picture of the terrorist organization slowly comes into focus.[8]
Of course the same techniques can also be used to plot 'Counter-terror' network of terror experts and their connections.
Marketing and data mining
According to an article for Realwire:
- Sales, marketing and customer retention campaigns are set to become smarter, more effective and more profitable thanks to a new social network analysis module from data mining automation vendor KXEN. By exploiting the connections between customers of telcos, banks, retailers and others, KXEN’s new KSN module has shown more than 15% lift improvement in campaign results.
- KSN identifies the otherwise hidden links – call records or bank transfers for instance – between friends, families, co-workers and other communities and extracts significant social metrics, pinpointing who are the best connected and who plays the most important role in any group. In this way it reveals valuable new customer intelligence that – when added to existing customer information – can strengthen significantly user organisations’ customer acquisition, retention, cross-sell and up-sell campaigns.
- Using KSN, companies can increase the accuracy and precision of their campaigns by leveraging the many more customer attributes that the module reveals, allowing them to better predict when customers may be about to churn to another provider, close an account, or buy a new product. A feature unique to KXEN allows the analysis of multiple networks and their evolution over time, exposing specific patterns of behaviors like rotational churn, fraud and identity theft.[9]
Fetishising Social Network Analysis
Bill Domhoff argued in 2005 that many present day adherents of social network analysis have forgotten its important links to questions of power:
- those who practice in the burgeoning field of network analysis ignore the early corporate interlock studies and continue to use hypothetical or small-group data for the most part while they hone their methodologies. It is as if these rigorous people are embarrassed by part of their early history.[10]
History
Resources
Email list
- Jiscmail list SNA 'The list will facilitate discussion of social network analysis amongst interested UK academics, and will facilitate organisation of off-line meetings.'
Software sources and information
- Social Netwotk Blog | Wikipedia Social network analysis software |
Visualisation
- http://sourceforge.net/projects/socnetv
- Mark Lombardi Global Networks
Data sources
- Letters written on behalf and in support of Scooter Libby to the judge that sat on his case: http://online.wsj.com/public/resources/documents/libbyletters20070605.pdf
Further Reading
- G william Domhoff How to do Power Structure Research, Who Rules America, May 2009.
- Robert A. Hanneman and Mark Riddle (2005) Introduction to social network methods Riverside, CA: University of California, Riverside ( published in digital form at http://faculty.ucr.edu/~hanneman/ )
- http://www.humanities.wisc.edu/programs/Faculty-Development-Seminars/representing-culture1/reading-list.html
- Scott, Social Network Analysis (excerpts)
- Scott Supplemental readings
- Bibliography This page is part of an on-line text by Robert A. Hanneman (Department of Sociology, University of California, Riverside) and Mark Riddle (Department of Sociology, University of Northern Colorado).
- Stephen P. Borgatti, Ajay Mehra, Daniel J. Brass, Giuseppe Labianca, et al 2009 Network Analysis in the Social Sciences Science 323, 892-895 (2009).
- Tom Snijders Social Network Analysis Website with details of information and downloads
- Steve Borgatti's Instructional Social Network Analysis Website.
- Stanley Wasserman and Katherine Faust , Social Network Analysis: Methods and Applications. Cambridge University Press, 1994.
- Peter Carrington, John Scott, Stanley Wasserman (eds.), Models and Methods in Social Network Analysis. Cambridge University Press, 2005.
- Alain Degenne and Michel Forse, Introducing Social Networks. Sage, 1999.
- John Scott, Social Network Analysis: A Handbook. 2nd edition. Sage, 2000.
- Wouter de Nooy, Andrej Mrvar, and Vladimir Batagelj, Exploratory Social Network Analysis with Pajek. Cambridge University Press, 2005
- The Back of the Napkin Blog Anti-social network analysis April 08, 2006
See Also
Notes
- ↑ Social Network Analysis, A Brief Introduction, orgnet.com, accessed 19 Mar 2010
- ↑ G William Domhoff 2005 http://sociology.ucsc.edu/whorulesamerica/powe/corporate_community.html Interlocking Directorates in the Corporate Community] Who Rules America? August
- ↑ Social Network Analysis, A Brief Introduction, orgnet.com, accessed 19 Mar 2010
- ↑ G William Domhoff 2005 Interlocking Directorates in the Corporate Community Who Rules America? August
- ↑ Breiger R. L. (1974). The duality of persons and groups. Social Forces, 53, 181-190.
- ↑ G William Domhoff 2005 Interlocking Directorates in the Corporate Community Who Rules America? August
- ↑ Connecting the Dots Tracking Two Identified Terrorists by Valdis Krebs, Orgnet.com, Original, 2002, updated in 2005, 2006, 2007
- ↑ Connecting the Dots Tracking Two Identified Terrorists by Valdis Krebs, Orgnet.com, Original, 2002, updated in 2005, 2006, 2007
- ↑ New Social Network Analysis Module Strengthens KXEN Automated Data Mining 24.03.2009 | Author: RealWire
- ↑ Domhoff, G. W. (2005) 'Power Structure Research and the Hope for Democracy' Who Rules America, April.